This option is available for both ePS-hosted (cloud) environments and self-hosted (standalone) environments.
If licensed, the integration option Authentication Pkg: LDAP and Login Bypass will be checked on the License page. For more information see Licensing.
When you are using Active Directory Services with Federated Identity Services, MarketDirect StoreFront communicates with one or more Active Directory Federation Servers (AD FS) that contain a directory of user information and associated privileges. When users log into MarketDirect StoreFront through, for instance, a company-branded URL, their credentials are authenticated against the appropriate Active Directory Federation Server, which in turn will communicate information on the user to MarketDirect StoreFront.
● Ideal for: ePS-hosted (cloud) sites that want to provide users with single sign-on (SSO) capabilities and authentication at the company level with each company pointed to its own Active Directory Federation Server (AD FS). Example: A commercial printer that has two or more company-branded sites and wants end users associated with those companies to be able to log in to the company-branded storefront with SSO. In this model, each company can have its own Active Directory server against which to authenticate company users.
● Site setup required: For the steps to set up Active Directory Authentication for ePS-hosted (cloud) or self-hosted (standalone) environments for cross-network authentication, see Active Directory Services with Federated Identity Services.
To use the Federated Identity Services authentication method, you must set up Active Directory Federation Service (AD FS). Please note that ePS will not assist with setup nor support of your AD FS setup or configuration. For more information, contact Microsoft.
MarketDirect StoreFront authenticates only that the user has access to his or her own account in the Directory Service database.
If you are not using LDAP services, make sure you have selected "MarketDirect StoreFront Internal Authentication" option in the Which authentication method to use for User Name and Password login form? field on the Site Settings | Authentication tab.
To configure Active Directory with Federated Identity Services
1 Go to Administration > Site Settings.
2 Open the Authentication tab.
3 Click Federated SSO.
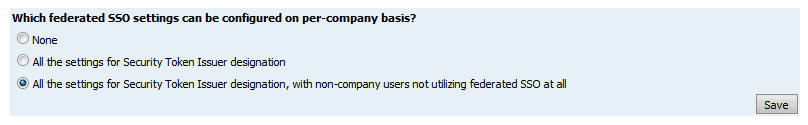
4 In the Which
federated SSO settings can be configured on per-company basis?
section, specify whether you want federated SSO to be set up at
the company-level (select one of the "All the settings..." options)
or at the site-level (select the None option).

● None: Select this option when all users of the site (across all companies) will use the federated ID system (site-level setting that impose federated SSO for all users).
● All the settings for Security Token Issuer designation: Select this option if you do not want companies (accessed via branded URLs) to use site-global settings but rather default to user name and password only. Note that you can enable and configure federated SSO separately for each company.
● All the settings for Security Token Issuer designation, with non-company users not utilizing federated SSO at all: Select this option if you want each company to provide its own settings (i.e., no site-level settings are imposed). Users not associated with a company will not use federated SSO at all. This lets you set up federated SSO for some companies but use internal (forms) authentication for others (requiring entry of user name and password).
5 In the Federation Server Connection section, configure the connection:
This section will not be shown if you selected the option All the settings for Security Token Issuer designation, with non-company users not utilizing federated SSO at all in the preceding step.
The settings in this section are site-level settings that govern how MarketDirect StoreFront connects with the federation system. Once the URL is entered, the fields will be automatically populated.
Federation Server's Metadata
You do not have to complete this step if you selected the option All the settings for Security Token Issuer designation, with non-company users not utilizing federated SSO at all in the previous step.
● Upload the federation metadata XML file:
● Click Browse... and, on the File Upload dialog, navigate to and select the federation metadata XML file.
The metadata XML URL depends on the ADFs server setup. Most of the time, if the ADFS server is myadfs.mycompany.com, the metadata URL will be found at https://myadfs.mycompany.com/FederationMetadata/2007-06/FederationMetadata.xml. This URL can be found in the ADFS server's ADFS 2.0 Manager in "AD FS 2.0 / Service / Endpoint" in the Metadata section.
● Click Open.
● Click Upload.
● Federation Protocol: Select the federated identity protocol to use for single sign-on.
● WS-Federation: WS-Federation stands for Web Services Federation Language. Select this option if your identity standard calls for WS-Federation.
For more information on WS-Federation, see https://msdn.microsoft.com/en-us/library/bb498017.
● SAML 2.0: SAML stands for Security Assertion Markup Language. Select this option if your identity standard calls for SAML 2.0.
This protocol supports the free and open source federated identity solution Shibboleth. For more information, visit http://www.shibboleth.net. SAML 2.0 is an XML-based protocol that uses security tokens containing assertions to pass information about a principal (usually an end user) between SAML Authority, in other words an identity provider, and a SAML Consumer, that is a service provider. SAML 2.0 enables web-based authentication and authorization scenarios including cross-domain single sign-on (SSO), which helps reduce the administrative overhead of distributing multiple authentication tokens to the user.
● Issuer Name ID: This is the ADFS server's unique identifier URL. It can be found in ADFS 2.0 Manager in "AD FS 2.0 / Service / Properties / General / Federation Service Identifier".
● Issuer Passive Redirect URL: The is the URL to which MarketDirect StoreFront will direct the web browser to request login. It can be found in ADFS 2.0 Manager in "AD FS 2.0 / Service / Endpoints / Token Issuance / SAML 2.0/WS-Federation".
● Valid Issuers: This is the list of issuer name IDs from which MarketDirect StoreFront will accept XML login tickets. This should typically contain a copy of Issuer Name ID.
● Token Signing Cert. Thumbprints: This is a hash/thumbprint of the ADFS server's token signing certificate. In can be found in ADFS 2.0 Manager in " AD FS 2.0 / Service / Certificates / Token-signing / View Certificate / Details / Thumbprint".
● Token Encryption Symmetric Keys: This is used only when XML login ticket encryption is manually set up. By default, MarketDirect StoreFront does not request the token encryption and this field should be left blank.
● Other Connection Settings
● Notify the federation server about the Logoff actions: Check to communicate when a user logs out to the federation server.
● Modify the Incoming Attributes/Claims: Map attributes and claims.
Example:
If you wanted to specify a Print Shop
for federated SSO:
1. In the Modify the Incoming Attributes/Claims
section: In the Original Name
field, enter urn:printshop and
in the New Name field enter [name of Print Shop
specified in Administration > Print Shops].
2. In the Rules for Mapping External
User Attributes to MDSF
User Profile Fields section: In the Print
Shop Name field, enter urn:printshop.
● Original Name
● New Name
● Click Save.
6 In the Rules for Mapping External User Attributes to MDSF User Profile Fields section:
When a directory services field is updated or deleted, the MarketDirect StoreFront User profile field will be automatically updated the next time the user logs into MarketDirect StoreFront.
The fields below are validated before assigning.
If specific values are not available in MDSF,
default values will be assigned to these fields:
●
Country
●
State/Province/Region
●
Company
●
Department (depends on Company)
●
Cost Center (depends on Company)
●
Print Shop Name
● From the Field pull-down list, select the MarketDirect StoreFront user profile field to map to the directory services profile field.
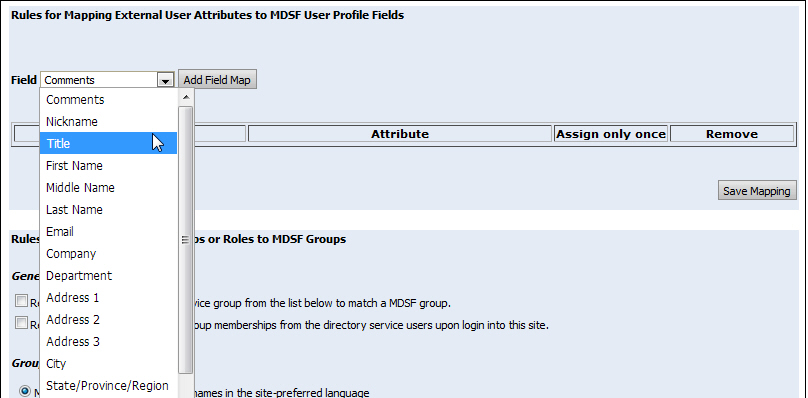
● Click Add Field Map.
● In the Attribute text entry field, enter the directory services profile field to the map with the selected profile field.
● For examples:
● First name would map to the directory services profile attribute givenName.
● Last name would map to sn.
● Email would map to mail.
● Company would map to company.
● Department would map to department.
● Country would map to c.
● Title would map to title.
● Address 1 would map to streetAddress.
● State would map to st.
● Zip/Postal code would map to postalCode.
● Phone Number 1 would map to telephoneNumber (e.g., office phone).
● Print Shop Name would map to an attribute urn:printshop.
For a complete list of directory services profile field names (i.e., attributes), search the Internet for "LDAP attributes" to consult a resource such as the one found here: http://computerperformance.co.uk/Logon/LDAP_attributes_active_directory.htm#LDAP_Attribute_.
7 Click Save Mapping.
To specify rules for mapping external groups or roles to MarketDirect StoreFront groups
These settings determine which groups users are assigned to (how users are mapped to MarketDirect StoreFront groups defined on your site) when they log in to the site.
1 Go to Administration > Site Settings.
2 Open the Authentication tab.
3 Click Federated SSO.
4 Scroll down to the Rules for Mapping External Groups or Roles to MDSF Groups section.
5 Configure the General Settings:
● Require at least one directory service group from the list below to match a MDSF group: Select this option to require that at least one of the directory service user groups matches a MarketDirect StoreFront user group listed below (i.e., Administrators, CSR, Operators, Registered Users, Rogo).
● Remove any un-matched MDSF group memberships from the directory service users upon login into this site: Select this option to remove any of the directory service user groups that do not match a MarketDirect StoreFront user group listed below when a user logs in to the site.
6 Configure the Group Matching Strategy settings:
● Match the MDSF groups by their names in the site-preferred language: Choose this option to have the MarketDirect StoreFront user groups mapped by their names in the default language for the site.
● Match the MDSF groups by their names in the language specified here: Choose this option to have the MarketDirect StoreFront user groups mapped by their names in a specific language, which you select from the language pull-down list.
● Use the list of external group names provided
for every MDSF
group: Choose this option to map the
MarketDirect StoreFront
user groups map to the names of the external groups (directory service
user groups) you enter in the External Group Names column of the matching
external groups table:
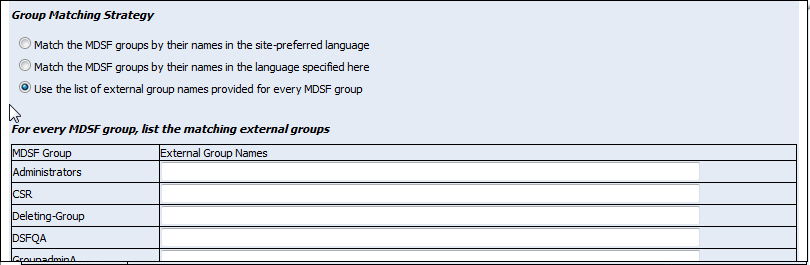
Separate multiple group names associated with a single MarketDirect StoreFront user group with a comma. If no group is to be mapped to a MarketDirect StoreFront user group, leave the blank empty.
7 Select the MDSF group allowed to be mapped to the external groups
This section will be hidden if you select
the Use the list of external group names
provided for every MDSF
group option in the Group Matching Strategy section.
This list will include all the groups from the Administration
> Groups page.
● Select the MarketDirect StoreFront user group(s) that you want to map with external groups (directory service user groups):
● Administrators
● CSR
● Operators
● Registered Users
● Click Save.
Specify which federated SSO login attempts should be logged
1 Specify which login attempts should be logged:
● None
● Only rejected login attempts
● All
2 Click Save.
3 To view a log of all federated SSO login attempts, click Federated SSO Attempted Login Log.
● For each login attempt, the log lists:
● Time
● IP Address
● Company
● Was Login Successful?
● Reason for Failure
If you have not already done so, specify the type of user authentication to use on your site: See Specify the Type of User Authentication to Use on Your Site for the steps to do so.